The security of your blog needs to be dealt with from the very beginning, not postponing it to a vague “spin up and get busy”. Especially since now in front of you detailed instructions about how to protect your wordpress site from hacking, viruses and other troubles.
I used to think about security, but not so seriously. And after this article on the website, A. Borisova took the matter seriously. I found on the Internet all the problem areas of the system and methods for their elimination. It turned out to be a rather large article of 14 points!
How to secure a wordpress website
1. Change the standard login. First of all, hackers break through such popular logins as admin, user, moderator, administrator. If you use one of them, then you have done half the work for the attackers. The admin is especially often used - short, easy to remember, you can immediately see that it is an important bump, so site owners do not change it to something more complex.
There are many options for changing this login, but the simplest one is:
- Go to the admin panel, go to the Users section - click Add.
- Come up with a complex login for the new user (you can just set letters and numbers), and select Role - Administrator.
- Log out of the current user (select Log out at the top right).
- Log in with the new user you just created.
- Work with this account: create new articles, edit old ones, add/remove plugins. In general, check whether he really has all the powers of the Administrator.
- Delete user with nickname admin.
2. Set a complex password- this is exactly the case when you cannot use your standard password in the form of qwerty. You need to come up with a unique password, very complex, of 20 characters with different case, numbers and different symbols. If you are afraid to forget, write it down in a paper notebook. But don't store it on your computer. How to come up with a complex password can be found in this article.
A complex password should be not only in the wordpress admin panel, but also for other services related to the site: mail, hosting, etc.
3. Hide login- no matter how you try to come up with a super complex login, there is a loophole that allows you to see it and copy it. To do this, enter http://your_domain.ru?author=1 in the address bar, substituting your domain. If the link does not turn into /author/admin, where admin is your new login, then everything is in order.
But if your login is still displayed there, you need to urgently hide it using a special command in the functions.php file:
/* Change login in comments */
function del_login_css($css) (foreach($css as $key => $class) (
if(strstr($class, "comment-author-insert_valid_login")) (
$css[$key] = 'comment-author-enter_fictitious_login'; ) )
return $css; )
add_filter('comment_class', 'del_login_css');
Now we set up a redirect to the main page, for this you need to open the .htaccess file in the root folder (using filezilla), and here after the line
RewriteRule . /index.php [L]
Add this text:
RedirectMatch Permanent ^/author/real_login$ http://your_domain.ru
4. Keep WordPress up to date. New versions appear from time to time, notifications hang right in the control panel. Make a backup copy of the site, update and check if it works. The newer, the more difficult it is to hack the system - new levels of protection appear, and old hacking techniques do not work.
5. Hide WordPress version from prying eyes. Default this information is displayed in the code of the pages, and attackers should not report it. Knowing your version, it will be easier for him to recognize gaps and hack the system.
So open functions.php for editing and then add this line:
remove_action('wp_head', 'wp_generator');
This simple function disables displaying system data.
6. Remove license.txt and readme.html from the root folder. They are not needed by themselves, but they can be used to easily read information about your system and find out the version of WordPress. They automatically reappear if you update wordpress. So clean up the files every time you install an update.
7. Hide the wp-includes, wp-content and wp-content/plugins/ folders. First, check if the contents of these folders are visible to outsiders. Just substitute your domain in the links and open the links in the browser:
- http://your_domain/wp-includes
- http://your_domain/wp-content
- http://your_domain/ wp-content/plugins
If you see folders and files when you go to these pages, then you need to hide the information. This is done very, very simply - create an empty file called index.php and place it in these directories. Now this file will be opened during the transition, i.e. blank page without any information.
8. Don't install free themes- it's already from personal experience information, although everyone writes about it. But I decided to bypass the system, and put a free theme from the Internet on my other site - I really liked it. And at first everything was fine.
After about six months, I began to check outgoing links from the site, and found 3 obscure links. I could not find them on the pages themselves - they hid them very cunningly. After studying the issue, I found information that this is a very common problem when code for remote placement of links is embedded in free templates. I had to spend the whole evening, but I fixed the problem and now everything is in order. But how much damage could it do!
9. Install the right protection plugins, but be sure to install from the official site ru.wordpress.org or from the control panel.
- Limit Login Attempts - to limit login attempts. If you enter your login and password incorrectly 3 times, access will be blocked for N minutes/hours. You set the number of attempts and blocking time yourself.
- Wordfence Security is a plugin for checking a website for viruses and malicious code changes. To start, just install and click Scan. But after checking, it is advisable to disable it so as not to create an additional load on the site. Check your blog for viruses at least once a month.
- WordPress Database Backup - automatically sends a backup copy of your website database to the mail. The frequency can be set independently - once a day or weekly.
- Rename wp-login.php - Changes the login address to the control panel from the standard http://your_domain/wp-admin.
- Anti-XSS attack - protects the blog from XSS attacks.
10. Check your computer for viruses– sometimes viruses come directly from your computer. So install a good antivirus program and keep it up to date.
11. Systematically back up– either using the WordPress Database Backup plugin, or manually. For some hosts, this happens automatically, so you can restore the site at any time in case of problems.
12. Work with a trusted host, because in many respects the security of the site depends on the quality of the hosting. I moved to Makhost a month ago, and the difference with the previous one is noticeable (the move was described in this article). I will not strongly recommend it, since I have not been with them for long, although a friend with them for a year cannot get enough of them. In general, do not take tariffs for 100 rubles for the sake of saving, then you can pay dearly.
13. Different mailboxes for the site and hosting. It is very easy to pull out a mailbox from WordPress, then you can hack it and gain access to data. And if the hosting is tied to it, it will not be difficult to change the password and take the site for yourself. So get a separate hosting box so that no one knows or sees it.
14. Connect a dedicated IP address, so as not to coexist with porn sites, sites under the filter or with viruses. So if you have the opportunity, get a separate IP so you don't have to worry about it. By the way, in the field of bloggers there are unconfirmed rumors that a dedicated IP improves positions in search results.
Now you know the most simple ways how to protect a site on wordpress, and you will be spared from banal threats. But besides this, there are many other dangers from which it is not so easy to save. Just for such serious situations, Yuri Kolesov created the course "
I was hacked. You know, like a page on VKontakte. But they did not beg for money, but created a lot of "left" pages with links to different sites. Then I thought about protecting my blog. And I found the perfect solution.
The first thing I did was to contact technical support with a request to restore my site the day before the hack, and ten minutes later I had my normal blog.
Then I installed a lot of plugins to protect WordPress from being hacked. But the blog has become terribly slow. Pages loaded in five to ten seconds. It is too long.
I started looking for plugins that do not load the system so much. I read reviews on these plugins and increasingly began to stumble upon All In One WP Security. According to the description, I really liked it and I decided to put it on my blog. And he still protects me, because I have not seen anything better.
What All In One WP Security can do (wordpress protection all in one):
- Makes database backups, configuration file wp-config. and .htaccess file
- Changing the address of the authorization page
- Hides WordPress Version Information
- Admin panel protection - blocking in case of incorrect authorization
- Robot protection
- And many more useful things
I can safely say that the All In One WP Security plugin is the best wordpress protection site.
Setting Up All In One WP Security
Having entered the Settings section, the first thing to do is to make backup copies:
- database;
- wp-config file
- htaccess file
This is done on the first page of the All In One WP Security plugin settings.
Make a backup (backup copy) before starting work
I will go through only the most important points.
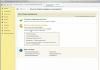
 all in one wp security plugin settings items
all in one wp security plugin settings items Control Panel
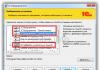
Here we are met by the “Safety Meter” counter. It shows the level of site protection. Your site must be at least in the green zone. No need to chase the maximum bar - extra settings can disrupt the functionality of the site. Get the golden mean.
 WordPress site protection counter
WordPress site protection counter When you change the plugin security settings, you will see a green shield with numbers in each item - these are the numbers that are added to the total security score.
 the figure is added to the total security score
the figure is added to the total security score Settings
WP Version Info Tab
Check the box Delete WP Generator metadata.
 Removing WP Generator Metadata
Removing WP Generator Metadata This is done so that the version of the WordPress engine you have installed is not displayed in the code. Attackers know which version has vulnerabilities, and knowing the version of WordPress you have installed will be able to hack your site faster.
Administrators
WP custom name
If you have a login to enter the admin panel admin, then be sure to change it. Admin is the most popular login. Many TsMSki offer it by default, and people are just too lazy to change it.
Attackers use various programs to hack websites. These programs pick logins and passwords until they find a suitable combination.
Therefore, do not use the admin login.
Display name
If your nickname matches the login, then be sure to change the login or nickname.
Password
If you enter your password here, the plugin will show how long it takes to hack your site.
Recommendations for strengthening password strength:
- Password must consist of letters and numbers
- Use uppercase and lowercase letters
- Do not use short passwords (minimum 6 characters)
- It is desirable to have special characters in the password (% # _ * @ $ and verbose)
 Password complexity
Password complexity Authorization
Authorization blocking tab
Be sure to include. If within 5 minutes someone enters the password incorrectly 3 times, then the IP will be blocked for 60 minutes. You can put more, but it is better not to do this. It may happen that you yourself enter the password incorrectly and then wait for months or even years :)
Check the box "Immediately block invalid usernames".
Let's say your login is hozyainsayta, and if someone enters another login (for example, login), then his IP address will be automatically blocked.
 authorization lock options
authorization lock options Automatic logout of users
We put a tick. If you log into the site admin panel from another computer and forget to log out of the admin panel, then after a specified period of time the system will log you out.
I put 1440 minutes (that's 24 hours).
 Options for automatically logging out users
Options for automatically logging out users User Registration
Manual confirmation
Check “Enable manual approval of new registrations”
 Manual approval of new registrations
Manual approval of new registrations CAPTCHA on registration
We also tick the box. This cuts off attempts to register a bot-robot, since robots cannot cope with the captcha.
Registration Honeypot (barrel of honey)
We celebrate. And we do not leave the robots not a single chance. This setting creates an additional invisible field (type Enter text here). This field is visible only to robots. Since they automatically fill in all the fields, they will write something in this field as well. The system automatically blocks those registration attempts for which this field is filled.
Database protection
DB table prefix
If your site has been around for a long time and there is a lot of information on it, then you should change the database prefix with the utmost care.
be sure to back up the database
If you have just created your site, you can safely change the prefix.
 Database table prefix
Database table prefix Database backup
Enable automatic backups.
Select the frequency of backups.
And the number of files with these backups that will be stored. Then they will start overwriting.
If you want these files to be additionally sent to your e-mail, then check the corresponding box. I have a separate folder in my mailbox for these purposes, all backups (of my and client sites) are sent there.
 Database backup settings
Database backup settings File system protection
Here we change the file permissions so that everything is green.

php file editing
We put in the event that you do not edit files through the admin panel. In general, you need to make any changes to files through ftp-managers programs (like a filezilla). So in case of any "jamb" you can always undo the previous action.
We deny access. With this action, we can hide important information for hackers.
Black list
If you already have IP addresses that you want to deny access to the site, then enable this option.
 Blocking users by IP
Blocking users by IP firewall
Basic firewall rules.
Firewall and Firewall is a software package that is a filter of unauthorized traffic.
These rules are added to the .htaccess file, so we back it up first.
Now you can put the necessary checkboxes:
 Activate Basic Firewall Features
Activate Basic Firewall Features  Protecting Against XMLRPC Vulnerability and WordPress Pingback
Protecting Against XMLRPC Vulnerability and WordPress Pingback  Block access to debug.log
Block access to debug.log Additional firewall rules
On this tab, check the following boxes:
- Disable directory browsing
- Disable HTTP tracing
- Disable comments through proxy
- Disable malicious strings in requests (May break the functionality of other plugins)
- Activate additional character filtering (We also act with caution, you need to look at how it affects the performance of the site)
- Each item has a button “+ More details” where you can read in detail about each option.
6G Blacklist Firewall Rules
We note both points. This is a proven list of rules that the WordPress site security plugin provides.
 Firewall (firewall) settings
Firewall (firewall) settings Internet bots
There may be problems with the indexing of the site. I don't enable this option.
Prevent hotlinks
We put a tick. So that images from your site are not shown on other sites via a direct link. This feature reduces the load on the server.

Detection 404
Error 404 (there is no such page) appears when you enter the page address by mistake. Hackers brute-force trying to find pages with vulnerabilities and therefore enter many non-existent URLs in a short period of time.
Such hacking attempts will be entered into a table on this page and by checking the box you will be able to block their IP addresses for the specified time.
 404 error tracking settings
404 error tracking settings Protection against brute force attacks
By default, all sites on WordPress have the same address of the authorization page. And so the attackers know exactly where to start hacking the site.
This option allows you to change the address of this page. This is a very good protection for a wordpress site. Be sure to change the address. I did not check this box, because mine automatically changed this page for me during the installation of the system.

Brute force protection with cookies
I did not turn on this setting, as there is a possibility of blocking myself when logging in from different devices.
CAPTCHA for login
If there are many users on your site or you have an online store, then you can enable Captcha during authorization in all points.
 Captcha protection during authorization
Captcha protection during authorization Whitelist for login
Log in to the admin panel only from your home computer and you are the only user of your site? Then enter your IP address and everyone else will be denied access to the authorization page.
It's funny sometimes things happen in life. I came across a cool course on Udemy on modern ways site protection and hacking. Upgrading my skill level, I missed the virus infection of my blog. Most likely, WordPress users have experienced the symptoms in one way or another, which I will describe next. If not, then you are lucky. I myself didn’t attach anything to sites for a very long time, thinking about how they still manage to infect their web resources. Back in 2014, I was surprised by messages on the forums that their site with an excellent attendance was simply infected and taken away.
And so, this morning, a letter arrived in the mail from my hoster, which puzzled me. Yes, I was pleasantly surprised that ihc monitors sites for malware, but the message that one file was changed at night without my knowledge and this suspicion of virus activity caused chaotic emotions. In fact, it was confirmation of my suspicions.
Some time ago, I discovered that the metric has clicks to sites that I just can’t write in my posts. When I tried to find these links stupidly through the blog search engine, I was redirected to Apache with an error message. Even then, suspecting something was wrong, I got into the file search.php active topic, in which I saw obfuscated code. Then it put me in a stupor, but due to lack of time, I did not delve further. As it turned out in vain. After all, this was one of the signs of infection.

An example of coded malware
I foolishly relied on the means of detecting malicious code from various services that litter the Internet. All of them "joyfully" informed me that the site was clean as morning dew.
Imagine a paradoxical situation - there is a non-working search function, there is an obfuscated php code so that the unlucky webmaster does not see the "gift", and anti-virus services are simply silent.
But back to our sheep, more precisely, to the sites. On all these sites I have two-level authorization. Maybe this saved the site from being taken away by a hacker. Two days after being infected search.php I received a notification from ihc.ru that some files have been changed and if I did nothing, it is recommended to check with the antivirus provided by the hosting itself. Well, now the opportunity to test this antivirus has turned up, it’s a pity that my favorite site got as a test subject 🙁
The result of the check, to put it mildly, rather puzzled me. Antivirus shoveled the site for about forty minutes and then sent its "verdict". 42 files were infected...
Here it was time to grab your head, thinking about how such a thing could have happened. It goes without saying that there was an exploit. But more about that later.
It was necessary to treat the site, but for this it had to be thoroughly investigated. Yes, it could have been done much easier - merge the database dump, transfer pictures from wp-content and re-upload all this to a freshly installed WordPress engine. But "easier" does not mean "better". In fact, without knowing what was changed, one would expect the hole to appear on the reuploaded site as well. And then it was just right to become a newly minted Sherlock Holmes in order to conduct a full audit of the site.

Finding malware is like being a detective
To be honest, I have not experienced such passion and interest for a long time. Yes, the hosting antivirus helped me in many ways, indicating in which files it found changes. But even he could not fully detect everything, since the code alternated with obfuscation and banal hex-coding using malicious js. It was necessary to do a lot with pens, using all third-party tools just as assistants.
So, we launch the code editor and look at the infected files. In fact, in the code they "fire" quickly enough due to their encryption. However, this is far from being the case everywhere. It happened that it was necessary to parse the php file code line by line and figure out what was wrong with it. I must say right away that it was with the theme files. In this case, the original theme files are very useful for comparison, if you are not sure exactly what this or that function is for (and a correctly written virus should inherit as little as possible).
But let's look at everything in order. I already posted a screenshot of the code obfuscated by the virus at the beginning of the article. Using the https://malwaredecoder.com/ resource, you can decode it into a digestible form and study it. In my case, some files contained the injection. We erase all this to hell.
However, sometimes you may come across a short code with an include. As a rule, they become infected index.php and wp-config.php. Unfortunately, I did not take a screenshot of such code, since at that time I did not plan to write an article. From this code, it was clear that this was the code for calling a specific file encoded through js. To decode the hexadecimal code, we will use the http://ddecode.com/hexdecoder/ service, with the help of which we will determine that the file is called at the address wp-includes/Text/Diff/.703f1cf4.ico(I omitted the full path, the essence itself is important). What do you think, is calling a simple icon file worth encoding, albeit relatively simple encoding? I think the answer is obvious and open this "icon" through the notepad. Naturally, this again turned out to be a fully encoded php. We delete it.
Having cleared the obvious files, you can move on to the not-so-obvious ones - the WordPress theme files. Here obfuscation is not used, you need to dig the code. In fact, if you do not know what the developer originally intended, then this task is very creative, although it can be solved quite quickly. If you haven't changed the theme code, it's easier to replace the infected files (the anti-virus identified them for sure) and move on. Or you can dig like me and find that very often such viruses are attributed to the file function.php absolutely left function, in which there will certainly be a code for accessing sql. In my case, it looks like this (formatting left unchanged):
$sq1="SELECT DISTINCT ID, post_title, post_content, post_password, comment_ID, comment_post_ID, comment_author, comment_date_gmt, comment_approved, comment_type, SUBSTRING(comment_content,1,$src_length) AS com_excerpt FROM $wpdb->comments LEFT OUTER JOIN $wpdb-> posts ON ($wpdb->comments.comment_post_ID=$wpdb->posts.ID) WHERE comment_approved=\"1\" AND comment_type=\"\" A ND post_author=\"li".$sepr."vethe". $comment_types."mes".$sepr."@".$c_is_approved."gm".$comment_auth."ail".$sepr.".".$sepr."co"."m\" AND post_password=\ "\" AND comment_date_gmt >= CURRENT_TIMESTAMP() ORDER BY comment_date_gmt DESC LIMIT $src_count";
Where this sample goes, we have already cleaned up. Therefore, we calmly look at which function this code is located in and delete this entire function - it was attributed to the malware. But, again, it is much easier and better to overwrite the entire file from the finished theme if you are afraid of breaking something.
Well, the final touch - check the number of site users. All my sites I have always led myself. Accordingly, there cannot and should not be any other users. However, given the infection, it is easy to guess that they will try to steal the site and create its own user with admin rights. In my case it turned out wp.service.controller.2wXoZ. We delete it.
A lot of work has been done, but is there an exhaust? Let's check again with an antivirus, which reports that no more viruses were found. Everything, the site is cured.
Results
As you can see, curing a site is quite simple, although time-consuming. After treatment, it is necessary to prevent such situations in the future. Here you need to take just a few steps:
- Update WordPress itself to latest version. It is possible that they used an exploit for an outdated engine.
- Check all plugins. Delete all unnecessary ones (which you put on the "future" and do not use) and check the relevance of those already working. However, even downloading a plugin from the WordPress repository does not give you a guarantee that the plugin will be clean. Cases have become more frequent when they buy out this or that plugin, make malware out of it, and when updating on your site, you will encounter the same “joys” as I do. In my case, I was infected just like that.
- Always check the subject. If public - update. Of course, it is better if you buy it on the same templatemonster, although this does not give 100% protection.
- Don't neglect tools like Wordfence. Although the free version of the plugin is very, very limited, at least you will know what is suspicious on your site.
- Once a month, do not be lazy to run the site through wpscan, to see what vulnerabilities appeared on it.
- Pay attention to the root of the site. There may be a file index.html.bak.bak. This also indicates that you have an infected site (you can immediately edit index.php, it is 100% infected)
- Do not trust public site antiviruses. There is little sense from them.
I tried to show by my example how you can cure a WordPress site. Antivirus on ihc.ru is just a malware scanner. But he also made things easy. Nevertheless, even if your hosting does not have such a service, you can identify and prevent infection using the above algorithm.
WordPress is one of the most popular content management systems (CMS) used by people either for simple blogging or for other purposes such as creating an online store. There are many plugins and themes to choose from. Some of them are free, some are not. Often these themes are downloaded by people who have customized them for their own benefit.
1. Theme Authenticity Checker (TAC)
Theme Authenticity Checker (TAC) is a WordPress plugin that scans the source files of each installed WordPress theme for hidden footer links and Base64 codes. Once detected, it displays the specific theme path, line number, and a small piece of malicious code, allowing the WordPress administrator to easily analyze this suspicious code. [Download ]
2.Exploit Scanner
Exploit Scanner is able to scan your site's files and database and is able to detect the presence of anything questionable. When using Exploit Scanner, keep in mind that it will not help prevent a hacker attack on your site and will not remove any suspicious files from your WordPress site. It is there to help identify any suspicious files uploaded by a hacker. If you want to delete them, you will need to do it manually. [Download ]

3. Sucuri Security
Sucuri is a well-established malware detection and security plugin in general. Sucuri's main features are monitoring files uploaded to a WordPress site, blacklist monitoring, security notifications, and more. It also offers remote malware scanning with the free Sucuri SiteCheck Scanner. The plugin also provides a powerful site firewall addon that can be purchased and activated in order to improve the security of your site. [Download ]

4.Anti-Malware
Anti-Malware is a WordPress plugin that can be used to scan and remove viruses, threats, and other malware that may be present on your site. Some of his important functions offer customized scans, full and quick scans, automatic removal of known threats. The plugin can be registered for free at gotmls . [Download ]

5.WP Antivirus Site Protection
WP Antivirus Site Protection is a security plugin for scanning WordPress themes along with other files uploaded to your WordPress site. The main features of WP Antivirus Site Protection are scanning every file uploaded to the site, updating the virus database on an ongoing basis, removing malicious code, sending notifications and alerts by email, and much more. There are also features that you can pay for if you want more “tightened” security for your site. [Download ]

6. AntiVirus for WordPress
AntiVirus for WordPress is an easy-to-use protection plugin that will help you scan the WordPress themes used on your site for malicious code. Using this plugin, you will be able to receive virus notifications in the admin panel. There is also a daily scan, according to the results of which you will receive an email if anything suspicious is found. [Download ]

7. Quttera Web Malware Scanner
The Quttera Web Malware Scanner will help you scan the site and protect it against the introduction of malicious code, viruses, worms, trojans and other computer evil spirits. It offers several interesting features such as scanning and detection of unknown malware, blacklisting, scanning engine with "artificial intelligence", detection of foreign external links and much more. You can scan your site for malware for free, while other services cost $60/year. [Download ]

8.Wordfence
If you are looking for a way to protect your site against cyber attacks, then you should try the Wordfence plugin. It provides real-time protection against known attacks, two-factor authentication, blocks the entire infected network (on detection), scans for known backdoors, and many other things. The services mentioned are free, but other features are offered for a fee. [Download ]

Using a security plugin protects your WordPress site from malware, attacks, and hacking attempts. This article collects the best WordPress security plugins that are recommended to use to secure your site.
Why Use a WordPress Security Plugin
Every week, about 18.5 million websites are infected with malware. The average site is attacked 44 times every day, including WordPress and other CMS websites.
A security breach on your website can cause serious business damage:
- Hackers can steal your data or data belonging to your users and customers.
- A hacked website can be used to distribute malicious code, infecting unsuspecting users with it.
- You may lose data, lose access to your website, the site may be blocked.
- Your site may be destroyed or damaged, which can affect SEO rankings and brand reputation.
You can scan your WordPress site for security breaches at any time. However, cleaning up a hacked WordPress site without professional help can be quite difficult for novice webmasters.
To avoid being hacked, you must follow site security guidelines. One of the important steps to secure your WordPress site is to use a security plugin. These plugins help simplify WordPress security and also block attacks on your site.
Let's take a look at some of the best WordPress security plugins and how they protect your site.
Note!
Note. You only need to use one plugin from this list. Having multiple active security plugins can lead to errors.
Note. You only need to use one plugin from this list. Having multiple active security plugins can lead to errors.
1. Sucuri

Sucuri is the leader in WordPress security. The developers offer a basic free plugin, Sucuri Security, which helps you harden your security and scans your site for common threats.
But the real value lies in the paid plans that come with the best WordPress firewall protection. A firewall helps block malicious attacks while accessing WordPress.
The Sucuri Internet Firewall filters out bad traffic before it reaches your server. It also serves static content from its own CDN servers. Security aside, their DNS layer firewall with CDN gives you an amazing performance boost and speeds up your website.
Most importantly, Sucuri offers to clean up your WordPress site if it gets infected with malware at no additional cost.
See also:
2.Wordfence

Wordfence is another popular WordPress security plugin. The developers offer a free version of their plugin that comes with a powerful malware scanner. The plugin detects and evaluates threats.
The plugin automatically scans your site for common threats, but you can also run a full scan at any time. You will be alerted if any signs of a security breach are found. You will also receive instructions on how to fix them.
Wordfence comes with a built-in WordPress firewall. However, this firewall is running on your server before loading WordPress. This makes it less effective than a DNS layer firewall like Sucuri.
3.iThemes Security

iThemes Security is a WordPress security plugin from the developers of the popular BackupBuddy plugin. Like all their products, iThemes Security offers a great clean user interface with tons of options.
It comes with file integrity checks, security hardening, login attempt restrictions, strong password enforcement, 404 error detection, attack protection, and more.
iThemes Security does not include a website firewall. It also doesn't include its own malware scanner, but uses the Sitecheck Sucuri malware scanner.
4. All In One WP Security

All In One WP Security is a powerful WordPress security checker, monitoring and firewall plugin. It makes it easy to apply basic WordPress security best practices to your website.
The plugin includes login blocking features to prevent attacks on your site, IP address filtering, file integrity monitoring, user account monitoring, scanning for suspicious database input patterns, and more.
It also comes with a basic website-level firewall that can detect and block some common patterns. However, it is not always effective and you will often have to manually blacklist suspicious IP addresses.
5. Anti-Malware Security

Anti-Malware Security is another useful WordPress anti-malware and security plugin. The plugin comes with actively maintained definitions that help you find the most common threats.
The plugin allows you to easily scan all files and folders on your WordPress site for malicious code, backdoors, malware, and other known malware attack patterns.
The plugin requires you to create a free account on the plugin's website. You will then have access to the latest definitions as well as some premium features such as attack protection.
Nuance: while the plugin does rigorous tests, it often shows a high number of false positives. Coordinating each of them with the source file is a rather painstaking work.
6 BulletProof Security

BulletProof Security isn't the prettiest WordPress security plugin on the market, but it's still useful with some great features. It comes with a setup wizard. The settings panel also includes links to extensive documentation. This will help you understand how security checks and settings work.
The plugin comes with a software scanner that checks the integrity of WordPress files and folders. It includes login protection, session timeout, security logs, and a database backup utility. You can also set up email notifications in security logs and receive alerts when a user is blocked.