Ministry of Education and Sciences of the Russian Federation
SEI "St. Petersburg State Polytechnic University"
Cheboksary Institute of Economics and Management (branch)
Department of Higher Mathematics and Information Technology
ESSAY
on the course "Information Protection".
on the topic: "Network analyzers"
Fulfilled
4th year student s/o 080502-51M
majoring in Management
at the enterprise of mechanical engineering"
Pavlov K.V.
checked
Teacher
Cheboksary 2011
INTRODUCTION
Ethernet networks have gained immense popularity due to their good bandwidth, ease of installation and affordable cost of installing network equipment.
However, Ethernet technology is not without significant drawbacks. The main one is the insecurity of the transmitted information. Computers connected to an Ethernet network are able to intercept information addressed to their neighbors. The reason for this is the so-called broadcast message exchange mechanism adopted in Ethernet networks.
Combining computers in a network breaks the old axioms of information protection. For example, about static security. In the past, a system vulnerabilities could be discovered and fixed by the system administrator by installing the appropriate update, which could only check the functioning of the installed "patch" only after a few weeks or months. However, this "patch" could be removed by the user accidentally or during work, or by another administrator when installing new components. Everything is changing, and now information technology is changing so fast that static security mechanisms no longer provide complete system security.
Until recently, firewalls were the main mechanism for protecting corporate networks. However, firewalls designed to protect an organization's information resources are often themselves vulnerable. This is because system administrators create so many simplifications in the access system that in the end the stone wall of the security system becomes full of holes like a sieve. Firewall protection (FW) may not be appropriate for high-traffic corporate networks, as the use of multiple FWs can significantly impact network performance. In some cases, it's better to "leave the doors wide open" and focus on methods for detecting and responding to network intrusions.
For continuous (24 hours a day, 7 days a week, 365 days a year) monitoring of a corporate network to detect attacks, "active" protection systems - intrusion detection systems are designed. These systems detect attacks on corporate network nodes and react to them in the manner specified by the security administrator. For example, they interrupt the connection with the attacking host, inform the administrator, or enter information about the attack in the logs.
1. NETWORK ANALYZERS
1.1 IP - ALERT 1 OR FIRST NETWORK MONITOR
First, let's say a few words about local broadcasting. On an Ethernet network, the computers connected to it typically share the same cable, which serves as a medium for sending messages between them.
Anyone wishing to transmit any message on a common channel must first make sure that this channel is in this moment free time. Having started transmission, the computer listens to the carrier frequency of the signal, determining whether the signal has been distorted as a result of collisions with other computers that are transmitting their data simultaneously with it. If there is a collision, the transmission is interrupted and the computer "silences" for a certain period of time in order to try to repeat the transmission a little later. If a computer connected to an Ethernet network does not transmit anything itself, it nevertheless continues to "listen" for all messages transmitted over the network by neighboring computers. Having noticed its network address in the header of the incoming data portion, the computer copies this portion to its local memory.
There are two main ways to connect computers to an Ethernet network. In the first case, the computers are connected using a coaxial cable. This cable is laid from computer to computer, connected to network adapters with a T-shaped connector and closed at the ends with BNC terminators. Such a topology is called a 10Base2 Ethernet network in the language of professionals. However, it can also be called a network in which "everyone hears everyone else." Any computer connected to a network is capable of intercepting data sent over that network by another computer. In the second case, each computer is connected by a twisted-pair cable to a separate port of the central switching device - a hub or switch. In these networks, called lOBaseT Ethernet networks, computers are divided into groups called collision domains. Collision domains are defined by hub or switch ports that are connected to a common bus. As a result, collisions do not occur between all computers on the network. and individually - between those of them that are included in the same collision domain, which increases the throughput of the network as a whole.
AT recent times in large networks, new types of switches began to appear that do not use broadcasting and do not close groups of ports to each other. Instead, all data transmitted over the network is buffered in memory and sent as soon as possible. However, there are still quite a few such networks - no more than 5% of the total number of Ethernet-type networks.
Thus, the data transmission algorithm adopted in the vast majority of Ethernet networks requires that each computer connected to the network continuously “listen” to everything without exception. network traffic. The access algorithms proposed by some people, when using which computers would be disconnected from the network while transmitting "foreign" messages, remained unrealized due to their excessive complexity, high cost of implementation and low efficiency.
What is IPAlert-1 and where did it come from? Once upon a time, the practical and theoretical research of the authors in the direction related to the study of network security led to the following idea: in the Internet, as in other networks (for example, Novell NetWare, Windows NT), there was a serious lack of software protection that implements complex control (monitoring) at the link level of the entire flow of information transmitted over the network in order to detect all types of remote influences described in the literature. Market research software network defenses for the Internet revealed the fact that such comprehensive remote impact detection tools did not exist, and those that did exist were designed to detect attacks of one specific type (for example, ICMP Redirect or ARP). Therefore, the development of an IP network segment control tool designed for use on the Internet and received the following name: network security monitor IP Alert-1 was started.
The main task of this tool, which programmatically analyzes network traffic in the transmission channel, is not to reflect remote attacks carried out over the communication channel, but to detect them, log (maintain an audit file with logging in a form convenient for subsequent visual analysis of all events associated with remote attacks on this network segment) and immediately signaling to the security administrator in case of detection of a remote attack. The main task of the network security monitor IP Alert-1 is to control the security of the corresponding segment of the Internet.
IP Alert-1 Network Security Monitor has the following functionality and allows, through network analysis, to detect the following remote attacks on the network segment controlled by it:
1. Control over the correspondence of IP and Ethernet addresses in packets transmitted by hosts located inside the controlled network segment.
On the IP Alert-1 host, the security administrator creates a static ARP table where he enters information about the corresponding IP and Ethernet addresses of hosts located inside the controlled network segment.
This feature allows you to detect unauthorized changes to the IP address or its substitution (the so-called IP Spoofing, spoofing, IP spoofing (jarg.)).
2. Control over the correct use of the remote ARP search mechanism. This function allows, using a static ARP table, to determine a remote "Rogue ARP server" attack.
3. Control over the correct use of the remote DNS lookup mechanism. This feature allows you to identify all possible types of remote attacks on the DNS service
4. Control over the correctness of remote connection attempts by analyzing transmitted requests. This feature allows you to detect, firstly, an attempt to investigate the law of changing the initial value of the TCP connection identifier - ISN, secondly, a remote "denial of service" attack carried out by overflowing the connection request queue, and, thirdly, directed " a storm" of false connection requests (both TCP and UDP) leading also to a denial of service.
Thus, the network security monitor IP Alert-1 allows you to detect, notify and log most types of remote attacks. At the same time, this program is in no way a competitor to Firewall systems. IP Alert-1, using the features of remote attacks on the Internet, serves as a necessary addition - by the way, incomparably cheaper - to Firewall systems. Without a security monitor, most attempts to carry out remote attacks on your network segment will remain hidden from your eyes. None of the well-known Firewalls is engaged in such intellectual analysis of messages passing through the network in order to detect various kinds of remote attacks, limited, at best, to logging, which records information about password guessing attempts, port scanning and network scanning with using well-known remote search programs. Therefore, if the IP network administrator does not want to remain indifferent and be content with the role of a simple extra in remote attacks on his network, then it is advisable for him to use the IP Alert-1 network security monitor.
Network packet analyzers, or sniffers, were originally developed as a means of solving network problems. They are able to intercept, interpret and save packets transmitted over the network for further analysis. On the one hand, this allows system administrators and technical support engineers to monitor how data is transferred over the network, diagnose and fix problems that arise. In this sense, packet sniffers are a powerful tool for diagnosing network problems. On the other hand, like many other powerful tools that were originally intended for administration, over time, sniffers have been used for completely different purposes. Indeed, a sniffer in the hands of an attacker is a rather dangerous tool and can be used to take over passwords and other confidential information. However, do not think that sniffers are some kind of magical tool through which any hacker can easily view confidential information transmitted over the network. And before we prove that the danger posed by sniffers is not as great as it is often presented, let's take a closer look at the principles of their functioning.
How packet sniffer works
Further in this article, we will consider only software sniffers designed for Ethernet networks. A sniffer is a program that works at the level of the NIC (Network Interface Card) network adapter (link layer) and stealthily intercepts all traffic. Because sniffers operate at the data link layer of the OSI model, they don't have to play by protocol rules anymore. high level. Sniffers bypass the filtering mechanisms (addresses, ports, etc.) that Ethernet drivers and the TCP/IP stack use to interpret data. Packet sniffers capture everything that comes through it from the wire. Sniffers can save frames in binary format and decrypt them later to reveal the higher level information hidden inside (Figure 1).

In order for the sniffer to be able to intercept all packets passing through the network adapter, the network adapter driver must support the promiscuous mode of operation (promiscuous mode). It is in this mode of operation of the network adapter that the sniffer is able to intercept all packets. This mode of operation of the network adapter is automatically activated when the sniffer starts or is set manually by the corresponding settings of the sniffer.
All intercepted traffic is passed to the packet decoder, which identifies and splits the packets into the appropriate levels of the hierarchy. Depending on the capabilities of a particular sniffer, the presented information about packets can subsequently be further analyzed and filtered.
Sniffer Limitations
Sniffers posed the greatest danger in those days when information was transmitted over the network in clear text (without encryption), and local networks were built on the basis of concentrators (hubs). However, those times are gone forever, and nowadays using sniffers to gain access to confidential information is by no means an easy task.
The fact is that when building local networks based on hubs, there is a certain common data transmission medium (network cable) and all network nodes exchange packets, competing for access to this medium (Fig. 2), and the packet sent by one network node is transmitted to all ports of the hub and this packet is listened to by all other nodes of the network, but only the node to which it is addressed receives it. Moreover, if a packet sniffer is installed on one of the network nodes, then it can intercept all network packets related to this network segment (a network formed by a hub).

Switches are more intelligent than broadcast hubs and isolate network traffic. The switch knows the addresses of the devices connected to each port and forwards packets only between the required ports. This allows you to offload other ports without passing every packet to them, as a hub does. Thus, a packet sent by a certain network node is transmitted only to the switch port to which the recipient of the packet is connected, and all other network nodes are unable to detect this packet (Fig. 3).

Therefore, if the network is built on the basis of a switch, then the sniffer installed on one of the network computers is able to intercept only those packets that are exchanged this computer with other network nodes. As a result, in order to be able to intercept packets that a computer or server of interest to an attacker exchanges with other network nodes, it is necessary to install a sniffer on this computer (server), which is actually not so simple. However, you should keep in mind that some packet sniffers are run from the command line and may not have GUI. Such sniffers, in principle, can be installed and run remotely and invisibly to the user.
In addition, you must also keep in mind that although switches isolate network traffic, all managed switches have a port forwarding or port mirroring feature. That is, the switch port can be configured in such a way that all packets arriving at other ports of the switch are duplicated on it. If in this case a computer with a packet sniffer is connected to such a port, then it can intercept all packets exchanged between computers in this network segment. However, as a rule, the ability to configure the switch is available only to the network administrator. This, of course, does not mean that he cannot be an intruder, but the network administrator has many other ways to control all users of the local network, and he is unlikely to monitor you in such a sophisticated way.
Another reason why sniffers are no longer as dangerous as they used to be is that nowadays the most important data is transmitted in encrypted form. Open, unencrypted services are rapidly disappearing from the Internet. For example, when visiting websites, the SSL (Secure Sockets Layer) protocol is increasingly used; SFTP (Secure FTP) is used instead of open FTP, and other services that do not use encryption by default are increasingly using virtual private networks (VPNs).
So, those who are worried about the possibility of malicious use of packet sniffers should keep the following in mind. First, to pose a serious threat to your network, sniffers must reside within the network itself. Secondly, today's encryption standards make it extremely difficult to intercept confidential information. Therefore, at present, packet sniffers are gradually losing their relevance as tools for hackers, but at the same time remain an effective and powerful tool for diagnosing networks. Moreover, sniffers can be successfully used not only to diagnose and localize network problems, but also to audit network security. In particular, the use of packet analyzers allows you to detect unauthorized traffic, detect and identify unauthorized software, identify unused protocols to remove them from the network, generate traffic for penetration testing to test the protection system, work with intrusion detection systems ( Intrusion Detection System, IDS).
Overview of Software Packet Sniffers
All software sniffers can be roughly divided into two categories: sniffers that support launching from the command line, and sniffers that have a graphical interface. At the same time, we note that there are sniffers that combine both of these features. In addition, sniffers differ from each other in the protocols they support, the depth of analysis of intercepted packets, the ability to configure filters, and the possibility of compatibility with other programs.
Typically, the window of any sniffer with a graphical interface consists of three areas. The first one displays a summary of the captured packets. Typically, this area displays a minimum of fields, namely: packet capture time; IP addresses of the sender and recipient of the packet; Packet source and destination MAC addresses, source and destination port addresses; protocol type (network, transport or application layer); some summary information about the intercepted data. The second area displays statistical information about the individual selected package, and finally, the third area presents the package in hexadecimal or character form - ASCII.
Almost all packet sniffers allow analysis of decoded packets (which is why packet sniffers are also called packet analyzers, or protocol analyzers). The sniffer distributes the intercepted packets by layers and protocols. Some packet analyzers are able to recognize the protocol and display the captured information. This type of information is usually displayed in the second area of the sniffer window. For example, any sniffer is able to recognize the TCP protocol, and advanced sniffers can determine which application generated this traffic. Most protocol analyzers recognize over 500 different protocols and can describe and decode them by name. The more information the sniffer is able to decode and present on the screen, the less you have to decode manually.
One problem that packet sniffers can run into is the inability to correctly identify a protocol using a port other than the default port. For example, in order to improve security, some well-known applications may be configured to use ports other than the default ports. So, instead of the traditional port 80 reserved for a web server, this server can be forced to reconfigure to port 8088 or any other. Some packet analyzers in this situation are not able to correctly determine the protocol and display only information about the lower level protocol (TCP or UDP).
There are software sniffers that come with software analytical modules as plug-ins or built-in modules that allow you to create reports with useful analytical information about intercepted traffic.
Other feature most software packet analyzers - the ability to configure filters before and after capturing traffic. Filters separate certain packets from the general traffic according to a given criterion, which allows you to get rid of unnecessary information when analyzing traffic.
tcpdump
The main tool for almost all network traffic collection is tcpdump . It is an open source application that is installed on almost all Unix-like operating systems. Tcpdump is a great data collection tool and comes with a very powerful filtering engine. It is important to know how to filter data during collection so that you end up with a manageable piece of data for analysis. Capturing all data from a network device, even on a moderately busy network, can generate too much data for simple analysis.
In some rare cases, tcpdump allows you to output the output directly to your screen, and this may be enough to find what you are looking for. For example, when writing an article, some traffic was captured and it was noticed that the machine was sending traffic to an unknown IP address. It turns out that the machine was sending data to the Google IP address 172.217.11.142. Since no Google products have been launched, the question arose as to why this is happening.
The system check showed the following:
[ ~ ]$ ps -ef | grep googleLeave your comment!
Original: 8 best packet sniffers and network analyzers
Author: Jon Watson
Publication date: November 22, 2017
Translation: A. Krivoshey
Date of transfer: December 2017
Packet sniffing is a colloquial term that refers to the art of sniffing network traffic. Contrary to popular belief, things like emails and web pages don't go through the Internet in one piece. They are broken into thousands of small data packets and thus sent over the internet. In this article, we'll take a look at the best free network analyzers and packet sniffers.
There are many utilities that collect network traffic, and most of them use pcap (on Unix-like systems) or libcap (on Windows) as their kernel. Another kind of utility helps analyze this data, since even a small amount of traffic can generate thousands of packets that are difficult to navigate. Almost all of these utilities differ little from each other in data collection, the main differences are in how they analyze the data.
Analyzing network traffic requires understanding how the network works. There is no tool that magically replaces an analyst's knowledge of basic networking, such as the TCP "3-way handshake" that is used to initiate a connection between two devices. Analysts also need to have some understanding of the types of network traffic on a normally functioning network, such as ARP and DHCP. This knowledge is important because analytics tools will simply show you what you ask them to. It's up to you to decide what to ask for. If you don't know what your network usually looks like, it can be hard to know that you've found what you're looking for in the mass of packages you've compiled.
The best packet sniffers and network analyzers
industrial tools
Let's start at the top and then go down to the basics. If you're dealing with an enterprise level network, you'll need a big gun. While almost everything uses tcpdump at its core (more on that later), enterprise-level tools can solve certain tricky problems, such as correlating traffic from multiple servers, providing intelligent queries to identify problems, alerting you to exceptions, and creating good graphs, which bosses always demand. .
Enterprise-level tools tend to focus on streaming network traffic rather than evaluating the contents of packets. By this, I mean that the main focus of most system administrators in an enterprise is to ensure that the network does not have performance bottlenecks. When such bottlenecks occur, the goal is usually to determine whether the problem is caused by the network or an application on the network. On the other hand, these tools can usually handle so much traffic that they can help predict when a network segment will be fully loaded, which is a critical point in network bandwidth management.
This is a very large set of IT management tools. In this article, the Deep Packet Inspection and Analysis utility is more appropriate, which is its integral part. Collecting network traffic is quite simple. With tools like WireShark, basic analysis is also not a problem. But the situation is not always completely clear. On a very busy network, it can be difficult to determine even very simple things, such as:
What application on the network is generating this traffic?
- if the application is known (say, a web browser), where do its users spend most of their time?
- which connections are the longest and overload the network?
Most network devices use the metadata of each packet to make sure that the packet goes where it needs to go. The contents of the packet are unknown to the network device. Another thing is deep packet inspection; this means that the actual content of the package is checked. In this way, critical network information that cannot be gleaned from metadata can be discovered. Tools like those provided by SolarWinds can provide more meaningful data than just traffic flow.

Other data-intensive network management technologies include NetFlow and sFlow. Each has its own strengths and weaknesses,
You can learn more about NetFlow and sFlow.
Network analysis in general is an advanced topic that draws both on the basis of acquired knowledge and on the basis of practical experience. It is possible to train a person in detailed knowledge about network packets, but if this person does not have knowledge of the network itself, and has no experience in detecting anomalies, he will not do very well. The tools described in this article should be used by experienced network administrators who know what they want but are not sure which tool is best. They can also be used by less experienced system administrators to gain day-to-day networking experience.
Basics
The main tool for collecting network traffic is
It is an open source application that is installed on almost all Unix-like operating systems. Tcpdump is a great data collection utility that has a very sophisticated filtering language. It is important to know how to filter data as you collect it so that you end up with a normal data set for analysis. Capturing all the data from a network device, even on a moderately busy network, can generate too much data that will be very difficult to analyze.
In some rare cases, it will be enough to print the data captured by tcpdump directly to the screen to find what you need. For example, while writing this article, I collected traffic and noticed that my machine is sending traffic to an IP address that I don't know. Turns out my machine was sending data to the Google IP address 172.217.11.142. Since I didn't have any Google products and didn't have Gmail open, I didn't know why this was happening. I checked my system and found the following:
[ ~ ]$ ps -ef | grep google user 1985 1881 0 10:16 ? 00:00:00 /opt/google/chrome/chrome --type=service
It turns out that even when Chrome is not running, it remains running as a service. I wouldn't have noticed this without packet sniffing. I captured a few more data packets, but this time I had tcpdump write the data to a file, which I then opened in Wireshark (more on that later). Here are the entries:

Tcpdump is a favorite tool of system administrators because it is a command line utility. tcpdump does not require a GUI to run. For production servers, the graphical interface is rather harmful, as it consumes system resources, so command-line programs are preferred. Like many modern utilities, tcpdump has a very rich and complex language that takes some time to master. A few of the most basic commands include selecting a network interface to collect data from and writing that data to a file so that it can be exported for analysis elsewhere. The -i and -w switches are used for this.
# tcpdump -i eth0 -w tcpdump_packets tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes ^C51 packets captured
This command creates a file with captured data:
File tcpdump_packets tcpdump_packets: tcpdump capture file (little-endian) - version 2.4 (Ethernet, capture length 262144)
The standard for such files is the pcap format. It is not text, so it can only be parsed by programs that understand this format.
3. Windump
Most useful open source utilities end up being cloned into others Operating Systems. When this happens, the application is said to have been migrated. Windump is a port of tcpdump and behaves in a very similar way.
The most significant difference between Windump and tcpdump is that Windump needs the Winpcap library installed before running Windump. Even though Windump and Winpcap are provided by the same maintainer, they need to be downloaded separately.
Winpcap is a library that must be pre-installed. But Windump is an exe file that doesn't need to be installed, so you can just run it. This is something to keep in mind if you are using a Windows network. You don't have to install Windump on every machine as you can just copy it as needed, but you will need Winpcap to support Windup.
As with tcpdump, Windump can display network data for analysis, filter in the same way, and write the data to a pcap file for later analysis.
4 Wireshark
Wireshark is the next best known tool in the sysadmin suite. It not only allows you to capture data, but also provides some advanced analysis tools. In addition, Wireshark is open source and has been ported to almost every existing server operating system. Called Etheral, Wireshark now works everywhere, including as a standalone portable application.
If you are analyzing traffic on a GUI server, Wireshark can do everything for you. He can collect data and then analyze it all right there. However, the GUI is rare on servers, so you can collect network data remotely and then examine the resulting pcap file in Wireshark on your computer.
When first launched, Wireshark allows you to either load an existing pcap file or run a traffic capture. In the latter case, you can additionally set filters to reduce the amount of data collected. If you don't specify a filter, Wireshark will simply collect all network data from the selected interface.

One of the most useful features of Wireshark is the ability to follow the stream. It's best to think of a thread as a chain. In the screenshot below, we can see a lot of captured data, but I was most interested in Google's IP address. I can right click and follow the TCP stream to see the whole chain.

If the traffic was captured on another computer, you can import the PCAP file using the Wireshark File -> Open dialog. The same filters and tools are available for imported files as for captured network data.

5.shark
Tshark is a very useful link between tcpdump and Wireshark. Tcpdump excels at data collection and can only surgically extract the data you need, however its data analysis capabilities are very limited. Wireshark does a great job of both capturing and analyzing, but it has a heavy user interface and cannot be used on non-GUI servers. Try tshark, it works on the command line.
Tshark uses the same filtering rules as Wireshark, which should come as no surprise since they are essentially the same product. The command below only tells tshark to grab the destination IP address and some other fields of interest from the HTTP part of the packet.
# tshark -i eth0 -Y http.request -T fields -e ip.dst -e http.user_agent -e http.request.uri 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox /57.0 /images/title.png 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /images/styles/phoenix.css 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /images/code/jquery_lightbox/jquery_lightbox/js/jquery-1.2.6.pack.js 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox /57.0 /images/styles/index.css 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /images/images/title.png 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /favicon.ico 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /favicon.ico
If you want to write the traffic to a file, use the -W option to do so, and then the -r (read) switch to read it.
Capture first:
# tshark -i eth0 -w tshark_packets Capturing on "eth0" 102 ^C
Read it here, or move it to another place for analysis.
# tshark -r tshark_packets -Y http.request -T fields -e ip.dst -e http.user_agent -e http.request.uri 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox /57.0 /contact 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /reservations/ 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100100 57.0 /reservations/styles/styles.css 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /res/code/jquery_lightbox/jquery_lightbox/js/jquery-1.2.6.pack. js 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /res/styles/index.css 172.20.0.122 Mozilla/5.0 (X11; Linux x86_64; rv:57.0) Gecko/20100101 Firefox/57.0 /res/images/title.png
This is a very interesting tool that falls into the category of network forensic analysis tools rather than just sniffers. The field of forensic science is typically investigative and evidence gathering, and Network Miner does this job just fine. Just as wireshark can follow a TCP stream to recover the entire chain of packet transfers, Network Miner can follow a stream in order to recover files that have been transferred over the network.

Network Miner can be strategically placed on the network to be able to observe and collect the traffic you are interested in in real time. It will not generate its own traffic on the network, so it will work in secret.
Network Miner can also work offline. You can use tcpdump to collect packets from a network point of interest and then import the PCAP files into Network Miner. Next, you can try to restore any files or certificates found in the recorded file.
The Network Miner is made for Windows, but with Mono it can be run on any OS that supports the Mono platform, such as Linux and MacOS.
There is a free version, entry-level, but with a decent set of features. If you need additional features such as geolocation and custom scenarios, you will need to purchase a professional license.
7Fiddler (HTTP)
It's not technically a network packet capture utility, but it's so incredibly useful that it's on this list. Unlike the other tools listed here, which are designed to capture network traffic from any source, Fiddler is more of a debugging tool. It captures HTTP traffic. While many browsers already have this capability in their developer tools, Fiddler is not limited to browser traffic. Fiddler can capture any HTTP traffic on your computer, including non-web applications.

Many desktop applications use HTTP to connect to web services, and other than Fiddler, the only way to capture such traffic for analysis is to use tools like tcpdump or Wireshark. However, they work at the level of packets, so for analysis it is necessary to reverse engineer these packets into HTTP streams. It can be a lot of work to do simple research, and this is where Fiddler comes in. Fiddler can help detect cookies, certificates, and other useful data sent by applications.
Fiddler is free and, like Network Miner, it can be run in Mono on almost any operating system.
8 Capsa
The Capsa Network Analyzer has several editions, each with different capabilities. At the first level, Capsa is free, and essentially allows you to simply capture packets and do some basic graphical analysis of them. The dashboard is unique and can help the inexperienced system administrator quickly identify network problems. The free tier is for people who want to learn more about packages and build up their analysis skills.

The free version allows you to control more than 300 protocols, suitable for email monitoring as well as saving email content, it also supports triggers that can be used to trigger alerts when certain situations occur. In this regard, Capsa can be used as a support tool to some extent.
Capsa is only available for Windows 2008/Vista/7/8 and 10.
Conclusion
It is easy to see how, using the tools we have described, a system administrator can create a network monitoring infrastructure. Tcpdump or Windump can be installed on all servers. A scheduler, such as cron or the Windows scheduler, starts a packet collection session at the right time and writes the collected data to a pcap file. The system administrator can then send these packets to the central machine and analyze them using wireshark. If the network is too large for this, there are enterprise-grade tools like SolarWinds to turn all network packets into a manageable dataset.
Read other articles about network traffic interception and analysis :
- Dan Nanni, Command Line Utilities for Monitoring Network Traffic in Linux
- Paul Cobbaut, Linux Systems Administration. Interception of network traffic
- Paul Ferrill, 5 Linux Network Monitoring Tools
- Pankaj Tanwar, Capturing Packets with the libpcap Library
- Riccardo Capecchi, Using Wireshark Filters
- Nathan Willis, Network Analysis with Wireshark
- Prashant Phatak,
Ministry of Education and Sciences of the Russian Federation
SEI "St. Petersburg State Polytechnic University"
Cheboksary Institute of Economics and Management (branch)
Department of Higher Mathematics and Information Technology
ESSAY
on the course "Information Protection".
on the topic: "Network analyzers"
Fulfilled
4th year student s/o 080502-51M
majoring in Management
at the enterprise of mechanical engineering"
Pavlov K.V.
checked
Teacher
Cheboksary 2011
INTRODUCTION
Ethernet networks have gained immense popularity due to their good bandwidth, ease of installation and affordable cost of installing network equipment.
However, Ethernet technology is not without significant drawbacks. The main one is the insecurity of the transmitted information. Computers connected to an Ethernet network are able to intercept information addressed to their neighbors. The reason for this is the so-called broadcast message exchange mechanism adopted in Ethernet networks.
Combining computers in a network breaks the old axioms of information protection. For example, about static security. In the past, a system vulnerabilities could be discovered and fixed by the system administrator by installing the appropriate update, which could only check the functioning of the installed "patch" only after a few weeks or months. However, this "patch" could be removed by the user accidentally or during work, or by another administrator when installing new components. Everything is changing, and now information technology is changing so fast that static security mechanisms no longer provide complete system security.
Until recently, firewalls were the main mechanism for protecting corporate networks. However, firewalls designed to protect an organization's information resources are often themselves vulnerable. This is because system administrators create so many simplifications in the access system that in the end the stone wall of the security system becomes full of holes like a sieve. Firewall protection (FW) may not be appropriate for high-traffic corporate networks, as the use of multiple FWs can significantly impact network performance. In some cases, it's better to "leave the doors wide open" and focus on methods for detecting and responding to network intrusions.
For continuous (24 hours a day, 7 days a week, 365 days a year) monitoring of a corporate network to detect attacks, "active" protection systems - intrusion detection systems are designed. These systems detect attacks on corporate network nodes and react to them in the manner specified by the security administrator. For example, they interrupt the connection with the attacking host, inform the administrator, or enter information about the attack in the logs.
1. NETWORK ANALYZERS
1.1 IP - ALERT 1 OR FIRST NETWORK MONITOR
First, let's say a few words about local broadcasting. On an Ethernet network, the computers connected to it typically share the same cable, which serves as a medium for sending messages between them.
Anyone wishing to send a message over a common channel must first make sure that this channel is free at the given time. Having started transmission, the computer listens to the carrier frequency of the signal, determining whether the signal has been distorted as a result of collisions with other computers that are transmitting their data simultaneously with it. If there is a collision, the transmission is interrupted and the computer "silences" for a certain period of time in order to try to repeat the transmission a little later. If a computer connected to an Ethernet network does not transmit anything itself, it nevertheless continues to "listen" for all messages transmitted over the network by neighboring computers. Having noticed its network address in the header of the incoming data portion, the computer copies this portion to its local memory.
There are two main ways to connect computers to an Ethernet network. In the first case, the computers are connected using a coaxial cable. This cable is laid from computer to computer, connected to network adapters with a T-shaped connector and closed at the ends with BNC terminators. Such a topology is called a 10Base2 Ethernet network in the language of professionals. However, it can also be called a network in which "everyone hears everyone else." Any computer connected to a network is capable of intercepting data sent over that network by another computer. In the second case, each computer is connected by a twisted-pair cable to a separate port of the central switching device - a hub or switch. In these networks, called lOBaseT Ethernet networks, computers are divided into groups called collision domains. Collision domains are defined by hub or switch ports that are connected to a common bus. As a result, collisions do not occur between all computers on the network. and individually - between those of them that are included in the same collision domain, which increases the throughput of the network as a whole.
Recently, in large networks, new types of switches have begun to appear that do not use broadcasting and do not close groups of ports to each other. Instead, all data transmitted over the network is buffered in memory and sent as soon as possible. However, there are still quite a few such networks - no more than 5% of the total number of Ethernet-type networks.
Thus, the data transfer algorithm adopted in the vast majority of Ethernet networks requires that each computer connected to the network continuously "listen" to all network traffic without exception. The access algorithms proposed by some people, when using which computers would be disconnected from the network while transmitting "foreign" messages, remained unrealized due to their excessive complexity, high cost of implementation and low efficiency.
What is IPAlert-1 and where did it come from? Once upon a time, the practical and theoretical research of the authors in the direction related to the study of network security led to the following idea: in the Internet, as in other networks (for example, Novell NetWare, Windows NT), there was a serious lack of software protection that implements complex control (monitoring) at the link level of the entire flow of information transmitted over the network in order to detect all types of remote influences described in the literature. A study of the Internet firewall software market revealed the fact that no such comprehensive remote impact detection tools existed, and those that did were designed to detect attacks of one specific type (for example, ICMP Redirect or ARP). Therefore, the development of an IP network segment control tool designed for use on the Internet and received the following name: network security monitor IP Alert-1 was started.
The main task of this tool, which programmatically analyzes network traffic in the transmission channel, is not to reflect remote attacks carried out over the communication channel, but to detect them, log (maintain an audit file with logging in a form convenient for subsequent visual analysis of all events associated with remote attacks on this network segment) and immediately signaling to the security administrator in case of detection of a remote attack. The main task of the network security monitor IP Alert-1 is to control the security of the corresponding segment of the Internet.
The IP Alert-1 network security monitor has the following functionality and allows, through network analysis, to detect the following remote attacks on the network segment it controls:
1. Control over the correspondence of IP and Ethernet addresses in packets transmitted by hosts located inside the controlled network segment.
On the IP Alert-1 host, the security administrator creates a static ARP table where he enters information about the corresponding IP and Ethernet addresses of hosts located inside the controlled network segment.
This feature allows you to detect unauthorized changes to the IP address or its substitution (the so-called IP Spoofing, spoofing, IP spoofing (jarg.)).
2. Control over the correct use of the remote ARP search mechanism. This function allows, using a static ARP table, to determine a remote "Rogue ARP server" attack.
3. Control over the correct use of the remote DNS lookup mechanism. This feature allows you to identify all possible types of remote attacks on the DNS service
4. Control over the correctness of remote connection attempts by analyzing transmitted requests. This feature allows you to detect, firstly, an attempt to investigate the law of changing the initial value of the TCP connection identifier - ISN, secondly, a remote "denial of service" attack carried out by overflowing the connection request queue, and, thirdly, directed " a storm" of false connection requests (both TCP and UDP) leading also to a denial of service.
Thus, the network security monitor IP Alert-1 allows you to detect, notify and log most types of remote attacks. At the same time, this program is in no way a competitor to Firewall systems. IP Alert-1, using the features of remote attacks on the Internet, serves as a necessary addition - by the way, incomparably cheaper - to Firewall systems. Without a security monitor, most attempts to carry out remote attacks on your network segment will remain hidden from your eyes. None of the well-known Firewalls is engaged in such intellectual analysis of messages passing through the network in order to detect various kinds of remote attacks, limited, at best, to logging, which records information about password guessing attempts, port scanning and network scanning with using well-known remote search programs. Therefore, if the IP network administrator does not want to remain indifferent and be content with the role of a simple extra in remote attacks on his network, then it is advisable for him to use the IP Alert-1 network security monitor.
So, the IPAlert-1 example shows how important network monitors are in network security.
Of course, modern network monitors support much more features, and there are quite a lot of them themselves. There are simpler systems, costing around $500, but there are also powerful systems equipped with expert systems capable of performing powerful heuristic analysis, their cost is many times higher - from $75,000.
1.2 CAPABILITIES OF MODERN NETWORK ANALYZERS
Modern monitors support many other features besides their basic ones by definition (which I reviewed for IP Alert-1). For example, cable scanning.
Network statistics (segment utilization rate, collision rate, error rate and broadcast traffic rate, determination of signal propagation speed); the role of all these indicators is that if certain threshold values are exceeded, we can talk about problems in the segment. This also includes checking the legitimacy of network adapters in the literature, if a “suspicious” one suddenly appears (checking by MAC address, etc.).
Frame error statistics. Short frames (shortframes) are frames that have a length less than allowed, that is, less than 64 bytes. This type of frames is divided into two subclasses - short frames with a correct checksum and short frames (runts) that do not have a correct checksum. The most likely reason for the appearance of such “mutants” is a malfunction of network adapters. Elongated frames, which are the result of a long transfer and indicate problems in the adapters. Ghost frames, which are the result of cable pickups. The normal percentage of erroneous frames in the network should not be higher than 0.01%. If it is higher, then either the network has technical malfunctions, or an unauthorized intrusion has occurred.
Collision statistics. Indicates the number and types of collisions on a network segment and allows you to determine the presence of a problem and its location. Collisions are local (in one segment) and remote (in another segment in relation to the monitor). Typically, all collisions in networks such as Ethernet are remote. The intensity of collisions should not exceed 5%, and peaks above 20% indicate serious problems.
There are many more possible functions, it is simply impossible to list them all.
I want to note that monitors are both software and hardware. However, they tend to play more of a statistical function. For example, LANtern network monitor. It is an easy to assemble hardware device, which helps supervisors and service organizations centrally maintain and maintain networks consisting of equipment from different manufacturers. It collects statistics and identifies trends to optimize network performance and expansion. Information about the network is displayed on the central management console of the network. Thus, hardware monitors do not provide adequate information protection.
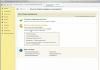
Microsoft Windows contains a network monitor (NetworkMonitor), however, it contains serious vulnerabilities, which I will discuss below.
Rice. 1. WINDOWS NT class network monitor.
The interface of the program is difficult to master on the fly.

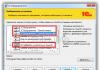
Rice. 2. View frames in the WINDOWS Network Monitor.
Most manufacturers are now striving to make their monitors have a simple and user-friendly interface. Another example is the NetPeeker monitor (not so rich in additional features, but still):

Rice. 3. Friendly NetPeeker monitor interface.
I will give an example of the interface of a complex and expensive NetForensics program ($95,000):

Fig.4. NetForensics interface.
There is a certain mandatory set of "skills" that monitors must have, according to today's trends:
1. At a minimum:
- setting traffic filtering templates;
- centralized management of tracking modules;
- filtering and analysis of a large number of network protocols, incl. TCP, UDP and ICMP;
- filtering network traffic by protocol, ports and IP addresses of the sender and recipient;
- abnormal termination of the connection with the attacking node;
- management of firewalls and routers;
- setting scenarios for handling attacks;
- attack recording for further playback and analysis;
- support for Ethernet, Fast Ethernet and Token Ring network interfaces;
- no requirement to use special hardware;
- establishing a secure connection between system components, as well as other devices;
- availability of a comprehensive database of all detected attacks;
- minimal network performance degradation;
- work with one tracking module from several management consoles;
- powerful reporting system;
- ease of use and intuitive graphical interface;
- low system requirements for software and hardware.
2. Be able to create reports:
- Distribution of traffic by users;
- Distribution of traffic by IP addresses;
- Distribution of traffic by services;
- Distribution of traffic by protocols;
- Distribution of traffic by type of data (pictures, videos, texts, music);
- Distribution of traffic by programs used by users;
- Distribution of traffic by time of day;
- Distribution of traffic by days of the week;
- Distribution of traffic by dates and months;
- Distribution of traffic by sites visited by the user;
- Authorization errors in the system;
- Logins and logouts.
Examples of specific attacks that network monitors can recognize:
Denial of service. Any action or sequence of actions that causes any part of the attacked system to fail, in which case it ceases to perform its functions. The reason may be unauthorized access, service delay, etc. Examples include SYN Flood, Ping Flood, Windows Out-of-Band (WinNuke) attacks, etc.
" Unauthorized access " (Unauthorized access attempt). Any action or sequence of actions that results in an attempt to read files or execute commands that bypass the established security policy. Also includes attempts by an attacker to gain privileges greater than those set by the system administrator. Examples are FTP Root attacks, E-mail WIZ attacks, etc.
"Preliminary actions before the attack" (Pre-attack probe)
Any action or sequence of actions to obtain information FROM or About the network (for example, usernames and passwords) used in the future to carry out unauthorized access. Examples are Port scan, SATAN scan, etc.
Suspicious activity
Network traffic that goes beyond the definition of "standard" traffic. May indicate suspicious activity on the network. Examples are Duplicate IP Address, IP Unknown Protocol events, and so on.
"Protocol analysis" (Protocol decode. Network activity that can be used to carry out one of the above types of attacks. May indicate suspicious activity on the network. An example is the events FTP User decode, Portmapper Proxy decode, etc.
1.3 HAZARDS OF NETWORK MONITORS
The use of network monitors is also fraught with potential dangers. If only because a huge amount of information passes through them, including confidential ones. Let's consider an example of a vulnerability on the example of the aforementioned NetworkMonitor, which is included in the distribution of Windows of the NT family. This monitor has a so-called HEX-panel (see Figure 2) that allows you to see frame data as ASCII text. Here, for example, you can see unencrypted passwords walking around the network. You can try, for example, reading the packages of the Eudora mail application. After spending a little time, you can safely see them in the open. However, one must always be on the alert, since encryption does not save either. Two cases are possible here. In the literature there is a slang term "obscene" - this is a neighbor of a certain machine in the same segment, on the same hub, or, as it is called now, a switch. So, if an “advanced” “hawk” decided to scan network traffic and retrieve passwords, then the administrator can easily identify such an attacker, since the monitor supports the identification of users using it. It is enough to press a button - and a list of "hackers-obscene" opens in front of the administrator. Much more complicated is the situation when an attack is made from outside, for example, from the Internet. The information provided by the monitor is extremely informative. A list of all captured frames is shown, sequence numbers of frames, times of their capture, even the MAC addresses of network adapters, which allows you to identify the computer quite specifically. The detailed information panel contains the "guts" of the frame - a description of its headers, etc. Even a curious novice will find much here familiar.
External attacks are much more dangerous, since, as a rule, it is very, very difficult to figure out the attacker. To protect in this case, you must use password protection on the monitor. If the Network Monitor driver is installed and no password is set, then anyone using the Network Monitor from the same distribution (same program) on another computer can connect to the first computer and use it to intercept data on the network. In addition, the network monitor must be able to detect other installations on the local network segment. However, this also has its own complexity. In some cases, the network architecture may suppress the discovery of one Network Monitor installation by another. For example, if the installed copy of Network Monitor is separated from the second copy by a router that does not allow multicast transmissions, then the second copy of Network Monitor will not be able to detect the first one.
Hackers and other intruders are not wasting their time. They are constantly looking for more and more new ways to disable network monitors. It turns out that there are a lot of ways, ranging from disabling the monitor by overflowing its buffer, ending with the fact that you can force the monitor to execute any command sent by the attacker.
There are special laboratories that analyze software security. Their reports are worrisome, as serious breaches are found quite often. Examples of real gaps in real products:
1. RealSecure is a commercial Intrusion Detection System (IDS) from ISS.
RealSecure is unstable when processing some DHCP signatures (DHCP_ACK - 7131, DHCP_Discover - 7132, and DHCP_REQUEST - 7133) supplied with the system. By sending malicious DHCP traffic, the vulnerability allows a remote attacker to disrupt a program. Vulnerability found in Internet Security Systems RealSecure Network Sensor 5.0 XPU 3.4-6.5
2. Program: RealSecure 4.9 network-monitor
Danger: High; Exploit: No.
Description: Several vulnerabilities have been identified in RS. The remote user can locate the device. The remote user can also define and change the configuration of the device.
Solution: Install an updated version of the program. Please contact the manufacturer.
1.4 PROTOCOL ANALYZERS, THEIR BENEFITS, DANGERS AND METHODS FOR PROTECTION FROM HAZARDS
Protocol analyzers are a separate class of software, although they are, in fact, part of network monitors. Each monitor has at least several protocol analyzers built into it. Why, then, use them if you can implement a more worthy system on network monitors? Firstly, it is not always advisable to install a powerful monitor, and secondly, not every organization can afford to purchase it for thousands of dollars. Sometimes the question arises as to whether the monitor itself will not be more expensive than the information it is designed to protect? It is in such (or similar) cases that pure protocol analyzers are used. Their role is similar to that of monitors.
The network adapter of each computer on an Ethernet network, as a rule, "hears" everything that its neighbors on the network segment "talk" about. But it processes and places in its local memory only those portions (so-called frames) of data that contain a unique address assigned to it in the network. In addition to this, the vast majority of modern Ethernet adapters allow operation in a special mode called promiscuous, in which the adapter copies all data frames transmitted over the network without exception to the computer's local memory. Specialized programs that put the network adapter into promiscuous mode and collect all network traffic for further analysis are called protocol analyzers.
The latter are widely used by network administrators to control the operation of these networks. Unfortunately, protocol analyzers are also used by attackers who can use them to intercept other people's passwords and other confidential information.
It should be noted that protocol analyzers pose a serious danger. The protocol analyzer could have been installed by an outsider who penetrated the network from outside (for example, if the network has access to the Internet). But it could also be the work of a "home-grown" attacker who has legal access to the network. In any case, the current situation should be taken seriously. Computer security specialists classify attacks on computers using protocol analyzers as so-called second-level attacks. This means that the computer hacker has already managed to penetrate the protective barriers of the network and is now looking to build on his success. With the help of a protocol analyzer, it can try to intercept user logins and passwords, their sensitive financial data (for example, credit card numbers) and confidential messages (for example, e-mail). With sufficient resources at its disposal, a computer intruder could, in principle, intercept all information transmitted over the network.
Protocol analyzers exist for any platform. But even if it turns out that a protocol analyzer has not yet been written for some platform, the threat posed by an attack on a computer system using a protocol analyzer still has to be considered. The fact is that protocol analyzers do not analyze a specific computer, but protocols. Therefore, the protocol analyzer can be installed in any network segment and from there intercept network traffic, which, as a result of broadcasts, enters every computer connected to the network.
Universities are the most common targets of attacks by computer hackers through the use of protocol analyzers. If only because of the huge number of different logins and passwords that can be stolen during such an attack. Using a protocol analyzer in practice is not as easy a task as it might seem. To be useful with a protocol analyzer, a computer intruder must have sufficient knowledge of network technology. It is impossible to simply install and run the protocol analyzer for execution, since even in a small local network of five computers, the traffic is thousands and thousands of packets per hour. And therefore, in a short time, the output of the protocol analyzer will fill the available memory "to the eyeballs". Therefore, a computer hacker typically configures the protocol analyzer to only intercept the first 200-300 bytes of each packet transmitted over the network. Usually, it is in the packet header that information about the user's login and password is placed, which, as a rule, is of most interest to the attacker. However, if an attacker has enough hard disk space at his disposal, then an increase in the volume of traffic intercepted by him will only benefit him and will allow him to learn a lot of interesting things in addition.
In the hands of a network administrator, a protocol analyzer is a very useful tool that helps him find and fix problems, get rid of bottlenecks that reduce network throughput, and promptly detect intrusions into it by computer hackers. How to protect yourself from intruders? You can advise the following. In general, these tips apply not only to analyzers, but also to monitors. First, try to get a network adapter that fundamentally cannot function in promiscuous mode. Such adapters do exist in nature. Some of them do not support promiscuous mode at the hardware level (there are a minority of them), and the rest are simply supplied with a special driver that does not allow promiscuous mode, although this mode is implemented in hardware. To find an adapter that does not have promiscuous mode, all you have to do is contact the technical support of any company that sells protocol analyzers and find out which adapters their software packages do not work with. Secondly, given that the PC99 specification, prepared in the depths of Microsoft and Intel corporations, requires the unconditional presence of promiscuous mode in the network card, purchase a modern network intelligent switch that buffers a message transmitted over the network in memory and sends it, as far as possible, to the exact address . Thus, the need for the adapter to "listen" to all traffic in order to extract from it messages addressed to this computer is eliminated. Thirdly, to prevent unauthorized introduction of protocol analyzers on network computers. Here you should use the tools from the arsenal, which is used to deal with software bookmarks and, in particular, with Trojans (installing firewalls). Fourth, encrypt all network traffic. There is a wide range of software packages that allow you to do this quite efficiently and reliably. For example, the ability to encrypt email passwords is provided by an add-on to the POP (Post Office Protocol) mail protocol - the APOP (Authentication POP) protocol. When working with APOP, a new encrypted combination is transmitted over the network each time, which does not allow an attacker to derive any practical benefit from the information intercepted using the protocol analyzer. The only problem is that today not all mail servers and clients support APOP.
Another product called Secure Shell, or SSL for short, was originally developed by the legendary Finnish company SSH Communications Security (http://www.ssh.fi) and now has many implementations available for free on the Internet. SSL is a secure protocol for the secure transmission of messages over a computer network using encryption.
Particularly famous are software packages designed to protect data transmitted over a network by encryption and combined by the presence of the abbreviation PGP in their name, which means Pretty Good Privacy.
It is noteworthy that there are worthy domestic developments in the family of protocol analyzers. A striking example is the Observer multifunctional analyzer (developed by ProLAN).

Rice. 5. Interface of the Russian analyzer Observer.
But, as a rule, most analyzers have a much simpler interface and fewer functions. For example, the program Ethereal.

Rice. 6. Interface of foreign analyzer Ethereal.
CONCLUSION
Network monitors, like protocol analyzers, are a powerful and efficient tool for administering computer networks, as they allow you to accurately evaluate many network operation parameters, such as signal speeds, collision areas, etc. However, their main task, which they successfully cope with, is to identify attacks on computer networks and notify the administrator about them based on traffic analysis. At the same time, the use of these software tools is fraught with potential danger, since, due to the fact that information passes through monitors and analyzers, unauthorized removal of this information can be carried out. The system administrator needs to pay due attention to protecting his network and remember that combined protection is much more effective. You should carefully consider the choice of traffic analysis software based on the real cost of information that is supposed to be protected, the likelihood of intrusion, the value of information for third parties, the availability of ready-made security solutions, and the organization's budget capabilities. A smart choice of solution will help reduce the likelihood of unauthorized access and will not be too "heavy" in terms of funding. It should always be remembered that today there is no perfect security tool, and this applies, of course, to monitors and analyzers. It should always be remembered that no matter how perfect the monitor is, it will not be ready for new types of threats, the recognition of which was not programmed into it. Accordingly, it is necessary not only to properly plan the protection of the network infrastructure of the enterprise, but also to constantly monitor the updates of the software products used.
LITERATURE
1. Attack on the Internet. I.D. Medvedkovsky, P.V. Semyanov, D.G. Leonov. - 3rd ed., erased. – M.: DMK, 2000
2. Microsoft Windows 2000 Administrator's Reference. Series "ITProfessional" (translated from English). U.R. Stanek. - M .: Publishing and trading house "Russian Edition", 2002.
3. Networking essentials. E. Tittel, K. Hudson, J.M. Stuart. Per. from English. - St. Petersburg: Publishing house "Peter", 1999
4. Information about breaches in software products taken from the SecurityLab server database (www.securitylab.ru)
5. Computer networks. Theory and practice. http://network-journal.mpei.ac.ru/cgi-bin/main.pl?l=ru&n=3&pa=9&ar=1
6. Network Analysis. Article in 2 parts. http://www.ru-board.com/new/article.php?sid=120
7. Electronic dictionary of telecommunication terms. http://europestar.ru/info/
8. Software and hardware methods of protection against remote attacks on the Internet. http://personal.primorye.ru/desperado/Xattack/7.2.htm
9. Security in the network monitor. Tutorial for WindowsXP. http://www.soft32.ru/literature.shtml?topic=windows&book=WinXP&page=Glava16/Index0.htm&subpage=Glava16/Index52.htm
10. Documentation for the RealSecure monitor. Provided by the manufacturer in electronic form upon request.
11. Security of computer systems. protocol analyzers. http://kiev-security.org.ua/box/12/130.shtml
12. Internet server of the Russian developer of analyzers - the company "ProLAN" http://www.prolan.ru/